In this post i will capture the installation of opendmarc and how its configure alongside Opendkim.
Install opendmarc
apt-get install opendmarc
Configure systemd service file
cat > /lib/systemd/system/opendkim.service <The specific changes here are lines #9 EnvironmentFile #13 -p $SOCKET
Defaults File
cat > /etc/default/opendmarc <Opendmarc Config file
cat > /etc/opendmarc.conf <Modify Postfix milters
If you are running both opendkim and opendmarc your milters will look like this:non_smtpd_milters = inet:127.0.0.1:12301, inet:127.0.0.1:12302 smtpd_milters = inet:127.0.0.1:12301, inet:127.0.0.1:12302Restart the service
systemctl daemon-reload systemctl restart opendmarc systemctl restart postfixDNS
Now go modify your DNS, adding a TXT record ‘_dmarc‘with the value ‘v=DMARC1; p=none; rua=mailto:postmaster@example.com‘
When you have validated dmarc is working properly you can change p=none to p=reject
How can you validate it?
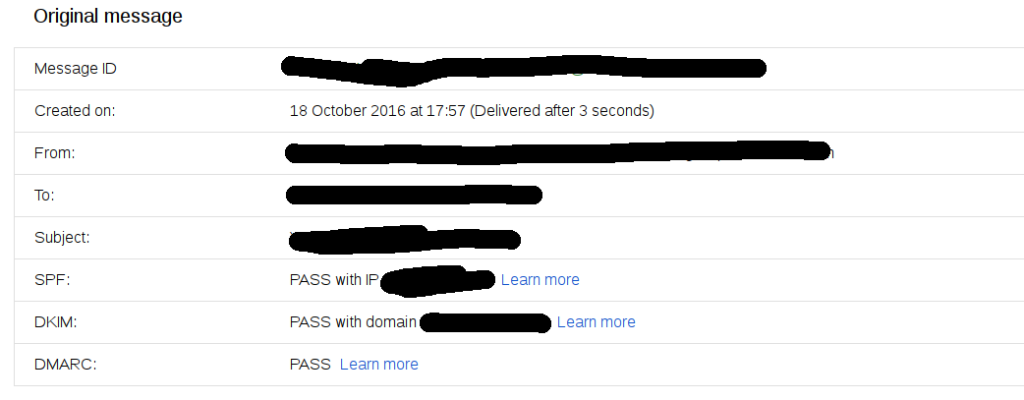
There are a number of tools online to help you with this, also you open up a mail in google and click ‘show original’.
Enjoy
Other resources
https://www.google.com/search?q=opendkim+setuphttps://www.google.com/search?q=opendmarc+setup